Blog
The Future of IT Outsourcing in Singapore: What Clients Expect in 2026
Jan 14, 2026

IT outsourcing in Singapore is shifting toward proactive and value-focused technology partnerships.
Read MoreA Singapore Guide to Sustainable Electronics
Nov 14, 2025

As tech consumers, it is our responsibility to play a supportive role in national sustainability goals through our daily choices and behaviors.
Read MoreWhat An Effective Data Backup Solution Looks Like
Oct 21, 2025

An effective backup solution balances data backup frequency, automation, and security to protect your data, prevent data loss, and support scalable enterprise backup strategies.
Read MoreWhy is IHP Important
Sep 15, 2025
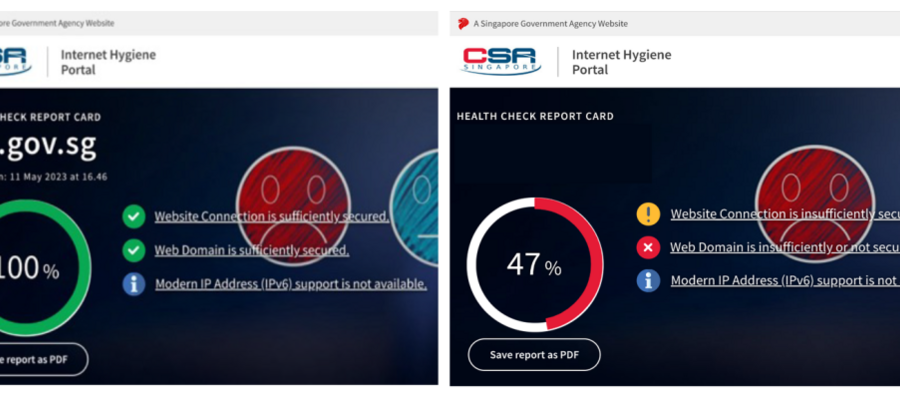
The Internet Hygiene Portal (IHP) launched by CSA, provides a one-stop, simplified platform for enterprises to check and improve their internet security.
Read MoreWhy Businesses Need Proactive IT Management
Aug 13, 2025

Proactive IT Management with system monitoring ensures a reduction in downtime and disruption of business operations and boosts productivity and business growth.
Read MoreFirewall Security Explained
Jul 10, 2025

Learn what firewall network security is, how it works, explore types of firewalls, and the best practices to protect your network from modern cyber threats
Read MoreWhy Data Backup is Crucial for Your Business
Jun 11, 2025

The best approach to tackling data loss scenarios is to deploy an effective data backup and recovery plan for robust data protection.
Read MoreManaged IT Service vs. Break-Fix
May 19, 2025

There are two popular models for handling IT support: managed IT services and break-fix. Both methods have strengths and weaknesses, and companies choose between them based on their needs. So, which IT support model is right for your business?
Read More